Exposure Management Platform for Vulnerability Management
Home » Exposure Management Platform for Vulnerability Management
Exposure Management Platform for Vulnerability Management
In the last decade threats have increased and evolved into a daily occurrence, therefore organisations need to make proactive cyber security a priority to protect data and digital assets. Having real-time visibility across all the digital surface is crucial to prevent cyber attacks and data breaches which can have devastating consequences.
An exposure management platform is the right tool to help companies discover any potential vulnerabilities and gaps in the attack surface. Efforts will be focused on the prevention of attacks, to ensure optimal business performance without interruptions. Vulnerability coverage spans web applications, cloud environments and resources, IT assets and identity systems such as active directory.
Vulnerability Management
Based on the risk-based approach, your security team needs to understand any exposures, and priorities which to fix first. In a timely manner, it is important to identify, investigate and prioritise the most critical vulnerabilities.
Find and fix vulnerabilities before a cyber attack happens. Real-time continuous assessment of your organisation’s digital surface is based on a strong engine with built-in prioritisation, threat intelligence and real-time insight all geared towards helping you understand your weaknesses and exposures. The next step is always to proactively prioritise remediations.
The platform’s intuitive dashboards help visualise scan results. Risk scores are presented to ensure you address vulnerabilities and immediately reduce risk. Embedded prioritisation capabilities ensure high-risk vulnerabilities are the first to be patched.
The dashboard is designed to offer an easy-to-understand risk score that will lead to a quick remediation before a potential breach takes place. Sign Up today, automate your workflows and start taking decisive actions.

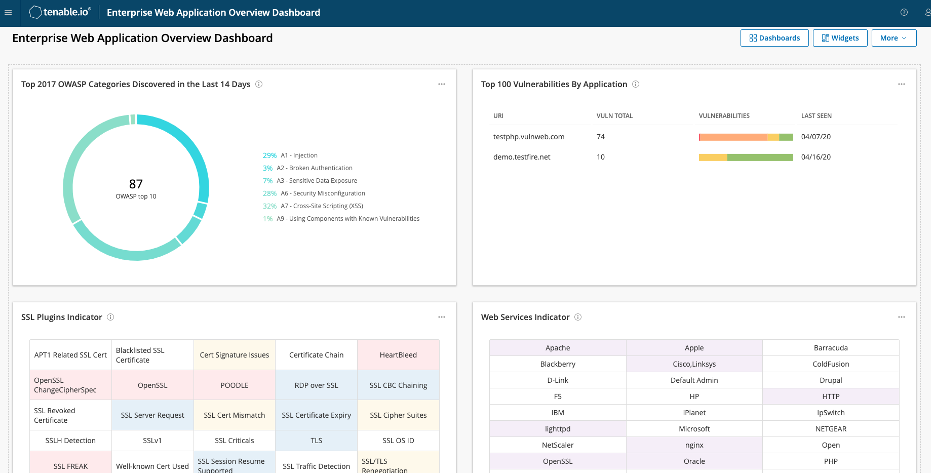
Web App Scanning
Web applications are one of the most useful and used digital touchpoints in any organisation, both public facing and internally for seamless operations.
Our Web Application Scanner is simple, scalable and offers automated vulnerability scanning. Gain a holistic and unified view of your IT and web application vulnerabilities for operational efficiency.
The top risks listed by OWASP Top 10 together with vulnerable web application elements and components and APIs used to push and get data, our tool provides a comprehensive and accurate assessment of web application vulnerabilities.
Cloud Security
Cloud security posture and vulnerability management through this low impact cloud agentless scanning. Threat detection and risk prioritisation are automated.
Our tool enables security teams to ongoingly assess the security posture of cloud environments. Gain full visibility across multi-cloud environments.
Adopt a cloud exposure management platform as part of your cloud journey. It will definitely help you accelerate cloud adoption, with security considerations. It aids development teams and devOps teams to accelerate deployments while maintaining high security and compliance standards.


Identity Exposure
(Active Directory)
Take full control of your active directory (AD) and Azure AD security and eliminate attack paths that can potentially lead to business-impacting issues.
This agentless Active Directory security solution allows security teams to see all the elements in your complex Active Directory environment, predict what matters to reduce risk and eliminate attack paths before malicious attackers exploit them.
This tool is geared to help find, prioritise and fix Active Directory weaknesses before attacks happen. It also offers step-by-step remediation guidance. Common attacks such as DCShadow, Brute Force, Password Spraying, and DCSync are detected for you to respond in real time. It enriches your SIEM, SOC or SOAR with attack insights so you can respond and stop attacks in a timely manner.
Book a demo
Don't just take our word for it - experience the power of our Exposure Management Platform firsthand with a personalized demo.
Our team of experts will guide you through the platform’s key features, demonstrate its capabilities in real-world scenarios, and tailor the experience to address your organization’s unique needs and challenges.
Requesting a demo is easy – simply submit a requestand let us show you how our platform can revolutionize your approach to Vulnerability Management and elevate your cybersecurity defenses to new heights.
Don’t wait until it’s too late – take proactive steps to protect your organization’s digital assets today. Request your personalized demo of our Exposure Management Platform now!
Frequently Asked Questions
One can opt for all products or any combination of the products into a single dashboard, as required.
Yes, get in touch with us for more information.
Most definitely, a free trial is available to gain familiarity with the platform.
Yes, a no obligation demo session can be scheduled. Get in touch.
Yes, data privacy and security are paramount in a Vulnerability and Exposure Management Platform. The platform itself undergoes rigorous security assessments to ensure it doesn’t introduce vulnerabilities
The platform provides: Actionable Insights, Workflow Management, Patch Management and Vulnerability Tracking.
The agentless assessment works for Amazon Web Services (AWS), Microsoft AZURE And Google Cloud Platform (GCP)
Absolutely, but also keep in mind that this does not replace annual penetration testing.
Yes the platform is versatile and can assess both on-premise and cloud environments and cloud-based apps.